I’ve been a fan of Cloudflare since around 2012/2013 when I started leveraging it for hosting DNS for all my web projects. Being able to instantly propagate changes was a game changer for me! Fast forward to 2019, and the EUCSE.com lab is leveraging Cloudflare free for DNS (CDN enabled), Domain Registration (wholesale prices are amazing!) and now Cloudflare Access for some of our more sensitive endpoints.
Modern IdP’s and EUC solutions such as Okta and VMware Workspace ONE are working hard to deliver a stunning User Experience as well as transforming security. Both have solutions that fully enable security at the edge, such as the VMware Unified Access Gateway for on-prem and Identity Manager for SaaS, and Okta’s strong modern authentication.
Now, say you have a service on the internet that you’d like to put behind some form of authentication, but dont want to add any changes to the product to integrate SAML or OAuth. Or, you have a service behind a VPN, and you’d like to remove that frustrating, legacy technology?
Step forward Cloudflare Access! For a detailed overview, read the overview here https://blog.cloudflare.com/introducing-cloudflare-access/. Essentially, Access ensures a connection is Authenticated, Authorised, and Encrypted meaning that a traditional VPN is no longer required!
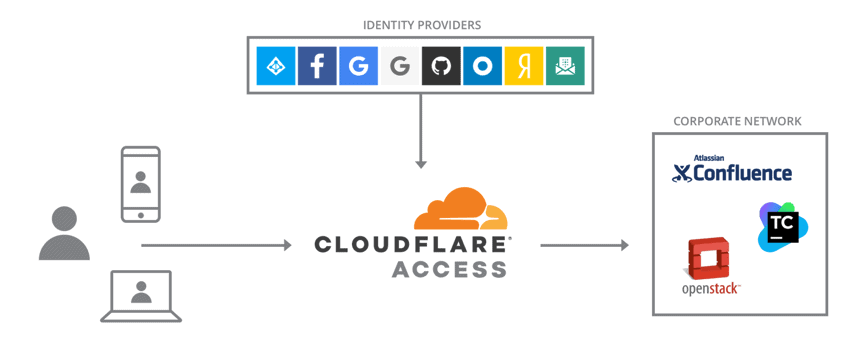
So, how can we get a page protected, authenticated via Okta on desktop, and seamlessly signed on (Mobile SSO) on a mobile device?
Set up Cloudflare
Get your domain on Cloudflare if it isn’t already. If you’re running a test lab or a UAT environment, I heavily recommend the free tier as you’re likely going to get all you need. Follow this guide: https://support.cloudflare.com/hc/en-us/articles/201720164-Step-2-Create-a-Cloudflare-account-and-add-a-website
Okta + Workspace ONE Config
This blog wont cover exactly step by step how to integrate WSO and Okta, but you can follow the below blogs to help.
- http://blog.tbwfdu.com/2018/12/enhancing-your-zero-trust-architecture.html – Keep an eye on Pete’s blog, he’s a rockstar!
- https://blog.eucse.com/workspace-one-okta-integration/
- https://docs.vmware.com/en/VMware-Workspace-ONE/services/WS1-IDM-deploymentguide/GUID-11D7ADF7-04B7-491B-AAFB-BBBC2FB27AB6.html
This can be done with other IdP’s as well, such as AzureAD and OneLogin if you have these.
Cloudflare Access IdP Setup
Click on Access from your Cloudflare Domain

Click on Manage Access and select your tier. We have gone with Premium to allow us to access Okta as an IdP. You also get 5 free users to test this out with forever, so if you have a lab or a team of less than 5, you’re good to go.
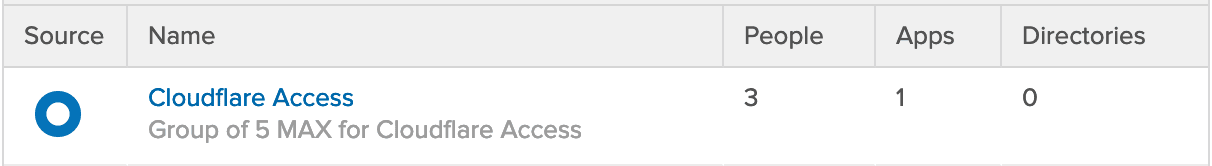
NOTE: The groups have to be ‘Okta Mastered’ to be leveraged by Cloudflare Access. Create a new Group within Okta and add your users to it. Groups from other sources within Okta are not supported (as far as I can work out)


Once this is done, you will be able to set up your Okta integration.

Follow the onscreen guide and it will get you there (remember, use the Okta URL without ‘-admin’, learn from my mistakes!)

Make sure the Save and Test is working for you:

You are good to go! You can leverage Instant Auth if you want to skip the selection box. I also removed the One Time Pin option.
Setup Access Policies
First, make sure CDN + DDoS is enabled on your root domain record.

Go back to Access, and set up your policy by clicking “Create Access Policy“
First, we will give it a name, and then select the location we want to protect. We can do subdomain (app.eucse.com) or subdirectory (eucse.com/app). The session duration is how long an auth session persists.

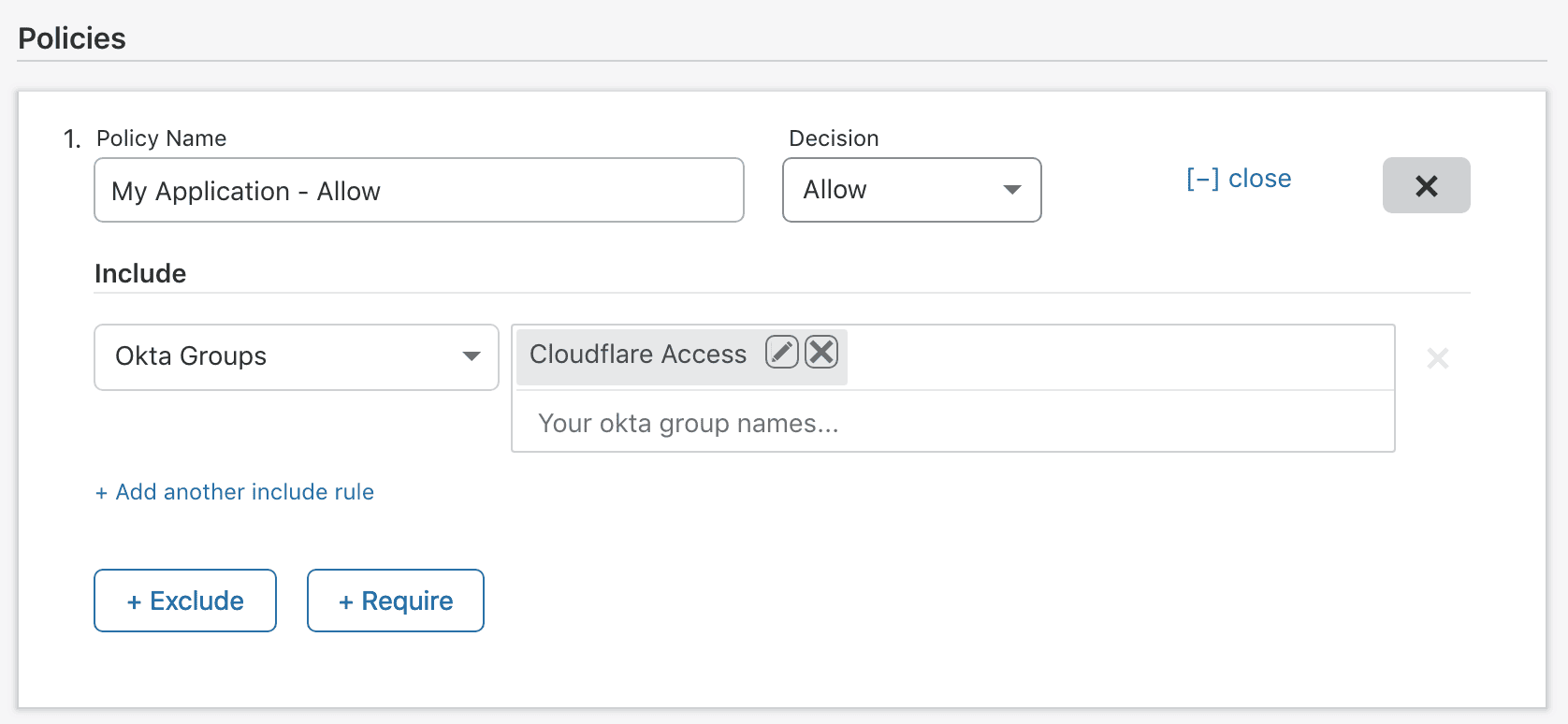
Next, set up Policies. In this example, we are giving access to our Okta mastered group “Cloudflare Access” to the Application Domain we have configured.
Configure Okta Routing for Mobile Devices
So, on desktop we’re going to login to the endpoint with our Okta login page as normal. However, we have Mobile SSO configured for our Workspace ONE UEM Managed devices, meaning users dont need to use their password, as long as the device is managed and secured by the UEM solution.
In Okta, head to your Admin panel. Select Users > Social and Identity Providers

Select Routing Rules tab and Click Add Routing Rule

Setup the Routing Rule as below. This will then route all requests from iOS, Android and Other mobile to the IdP Workspace ONE. Workspace ONE is then configured for Mobile SSO as per the above links.

And you’re done! See the below video for a demo.
In this example, we have secured https://eucse.com/cloudflare
Any questions or comments please leave them below, or reach out to us on Twitter at @EUCSE1 or @AdamPMatthews
Solutions Engineer @ Okta. Former SE at VMware for Workspace ONE. All things Identity, MDM and Mac. Occasionally takes photos of Bands at adammatthews.photography, and blogs at adammatthews.co.uk.