This article has been updated to match the new Azure admin portal – ENJOY!
Workspace One UEM allows for a whole number of different ways to authenticate when enrolling new devices. The majority of organisations will always choose to integrate with their on-premise AD through the use of the Could Connector, this component allows for user group sync, integration to on premise certificate authorities and to pull user attributes from Active Directory. All these features allow for a very stream lined enrollment and the ability to integrate with a whole number of different corporate resources.
However,
For a lot of new organisations, that may not already have a large on-premise foot print, cloud directories are far more favourable. They’ll skip the need and high cost for internal equipment when they can easily spin up new tenants on whatever identity/directory service they choose.
An ever increasing solution is Azure Active Directory online only, with no on-premise directory sync (though Azure AD Connect). Leveraging this cloud directory type, allows users to authenticate into Workspace One UEM using SAML, this creates the user within the console and allows the user to enroll their devices.
Setting this up can be complicated and detailed instructions can be hard to find. Don’t worry, the EUCSE’s got your back!
Add Azure Application:
1 .Go to the Azure portal by clicking the following link: https://portal.azure.com.
2. Once logged in, select “Azure Active Directory” on the left-hand side of the portal
3. Select the Enterprise Applications section in the panel on the left and then select the “+New Application” button at the top.

4. Select ‘Non Gallery Application’ and give it a name. This will enable you to setup the SAML integration.

5. Select ‘Add’ – Be patient, this can take a few seconds. The bell icon in the top bar will display whats happening with the app. You’ll then automatically be re-directed to the app configuration screen when it’s completed.
Configure Azure Application

- You should then see the above display. An overview of the new app.
- Now click on point 2. ‘Set up single sign on’
- You’ll then be asked what method of single sign on you require.

4. Select SAML and you’ll be shown the following screen.

5. Scroll down to point 3 and hit download on ‘Federation Metadata XML’ – We’ll now need to upload this into Workspace ONE UEM.
Workspace One UEM Configuration
- Open your console, go to Groups & Settings -> All Settings -> System -> Enterprise Integration -> Directory Services
- Change “Directory Type” to “none” and save the page at the bottom.
- Scroll back up and enable “Use SAML for Authentication”
- Enable “Use new SAML Authentication Endpoint”
- Under SAML 2.0 you can upload the XML you just saved from the Azure App and select Upload next to Import Identity Provider Settings

6. Now scroll to the bottom and save. The imported XML settings will be applied only after saving the Directory Services page. The Identity Provider ID and the SAML information should now be populated from the federation XML you just uploaded.
Directory Services Configuration
1 – Now scroll down and make sure that the request binding and response are both set to ‘Post’ and hit save.

2-Previously we would have needed to manually add the assertion URLs into Azure but we can do this automatigically now! Scroll down to the bottom of the directory page in UEM and click’Export Service Provider Settings’ – We’ll use this shortly to finish the Azure App configuration.
3. Now we need to update the user attribute section. Select the User tab at the top and change the user attributes and Base DN as seen in the screenshot below:
- Change the BASE DN to the following: WAAD
- Object Identifier – http://schemas.microsoft.com/identity/claims/objectidentifier
- Username and Email Address – http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
- Display Name and First Name – http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
- Last Name – http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname

Final Azure App Configuration
1-Make sure you’re on the ‘Single Sign-on’ page of your app and click on ‘Upload metadata file’

2- This should essentially complete the final section of your Azure app. Uploading the metadata should fill all the response URL’s required.
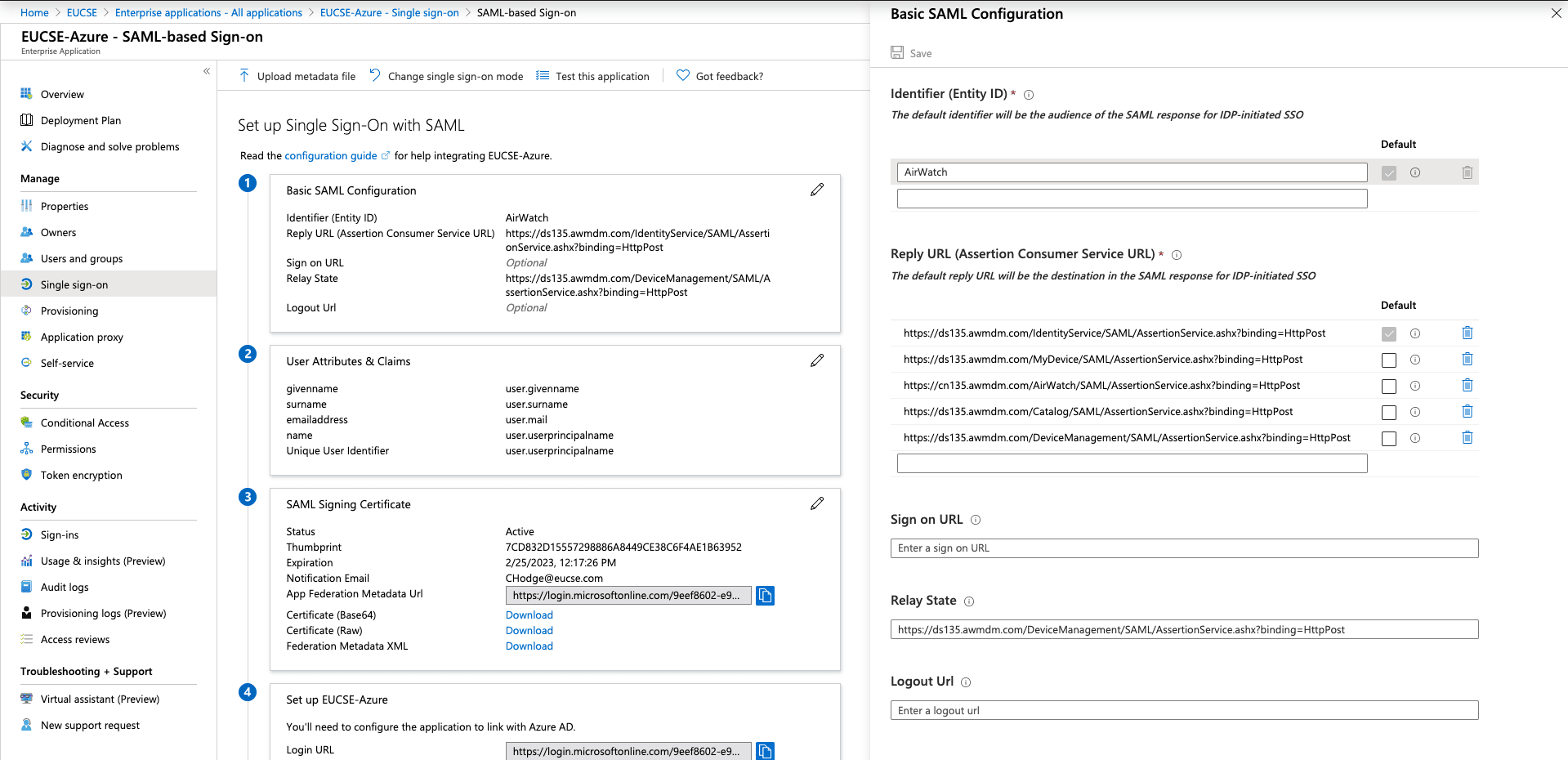

SAML Authentication Test
- Get a hold of any device type
- Download the Workspace One Intelligent Hub application
- Select Server Details on the Agent page (if you have AutoDiscovery you can select email instead)
- Enter your environment URL along with your group id where you configured Azure SAML Authentication.
- You should now be re-directed to the Azure logon page. Once here enter in the credentials for a user in Azure.
You can also test this from a computer by navigating to: https://dsyourenvironment.awmdm.com/enroll?GID=GROUPID
You should then be forwarded to a Microsoft login page

Sales Engineer specialising in Unified Endpoint Management (UEM) and Identity Management.
Technical Expertise:
o Okta – Identity Management – Providing single sign on services to applications
o VMware Workspace ONE – Configuring and managing AirWatch components across all device types.
o Digital Transformation – Helping organisations implement and deploy a modern strategy for UEM
o Networking – VPN, DNS, DHCP
o Device Management – macOS, iOS, Android, Windows and Rugged Devices
o Cloud Solutions – Azure, Office 365, Identity Providers, VMware AirWatch
o Server – Windows Server, Active Directory, Exchange

Shaun Attwood
December 2, 2019Hi, is an Azure AD P1/P2 subscription required for this integration? Or is Azure AD basic subscription good enough?
Peter Meuser
September 25, 2020Hi Charlie, looks like Azure Portal doesn’t create SAML signing certificate, before the missing basic SAML config is given. It might be time to redo your guide. I am just wondering, why there seems to be no official VMware integration doc for AAD where everybody is on O365.
Peter
MD
October 29, 2020Great doc, thanks!!! This was an impossible find!
Charlie Hodge
October 29, 2020No worries at all! Glad you found it useful! ?
MD
October 30, 2020Just one minor comment, as mentioned by Peter, in the “Scroll down to point 3 and hit download on ‘Federation Metadata XML’ – We’ll now need to upload this into Workspace ONE UEM.” step, it looks like we just need to create the certificate prior by clicking on “Add a certificate”.
The only question I am not 100% sure on is what type of certificate you used, here are the options:
Sign SAML response
Sign SAML assertion (Default)
Sign SAML response and assertion
Thanks
Michael
November 4, 2020Thanks for the guide, I found it by chance and it helped my a day ago. It has worked for two days or so and now I’m getting the error : SAML authentication has timed out; please try your request again.
It happens when I’m testing the application : https://ds2148.awmdm.com/IdentityService/SAML/AssertionService.ashx?binding=HttpPost
I’ve redo the configuration again and again with the same procedure and can’t get it work again. When I’ve created the certificate I’ve tried all options but no luck 🙁
Suliman Ali Shah
April 9, 2021Hi Michael. Did you get any solution for your issue . (SAML authentication has timed out; please try your request again.) I m also having it .
macOS Custom Enrolment with Workspace ONE, Okta and more – EUCSE Blog
November 25, 2020[…] https://blog.eucse.com/azure-saml-into-workspace-one-uem/ […]
Robert James Battam
January 3, 2024SO what if you don’t have a “Groups” tab, and only the “Users” tab? anyone have this issue?